CTS CRF Compliance
Navigating the requirements of the Communications, Space, and Technology Commission's Cybersecurity Regulatory Framework (CRF) and achieving compliance

CST CRF

Formerly known as the Communications and Information Technology Commission (CITC), the Communicatios, Space & Technology Commission (CST) is the regulatory body for the Information and Communications Technology (ICT) and postal sectors in Saudi Arabia. It issues the Cybersecurity Regulatory Framework (CRF), which applies to all licensed and registered service providers operating within these sectors.
The first version of the CRF was issued in June 2020, while the second version (newest) was issued in October 2023. This framework is a cornerstone of the CST's efforts to bolster the cybersecurity posture of the Information and Communications Technology (ICT) sector in Saudi Arabia.
The CRF provides requirements for better managment of Cybersecurity risks through a consistent approach and inline with international standards and best practices.
Who Should Comply With CST CRF?
The provisions of the CST CRF apply to Service Providers (SPs) subject to CST's regulatory authority, specifically targeting licensed and registered service providers within the ICT and postal sectors. A key distinction is that the CRF primarily targets organizations that are not classified as Critical National Infrastructure (CNI). Organizations classified as CNIs are typically required to comply with the National Cybersecurity Authority's (NCA) Essential Cybersecurity Controls (ECC).
Need more details? Review the CST CRF:
If you cannot find what you want, please visit the CST website
You can also read the Regulations for Cybersecurity Operations in ICT Sector (English)
Understanding CST CRF
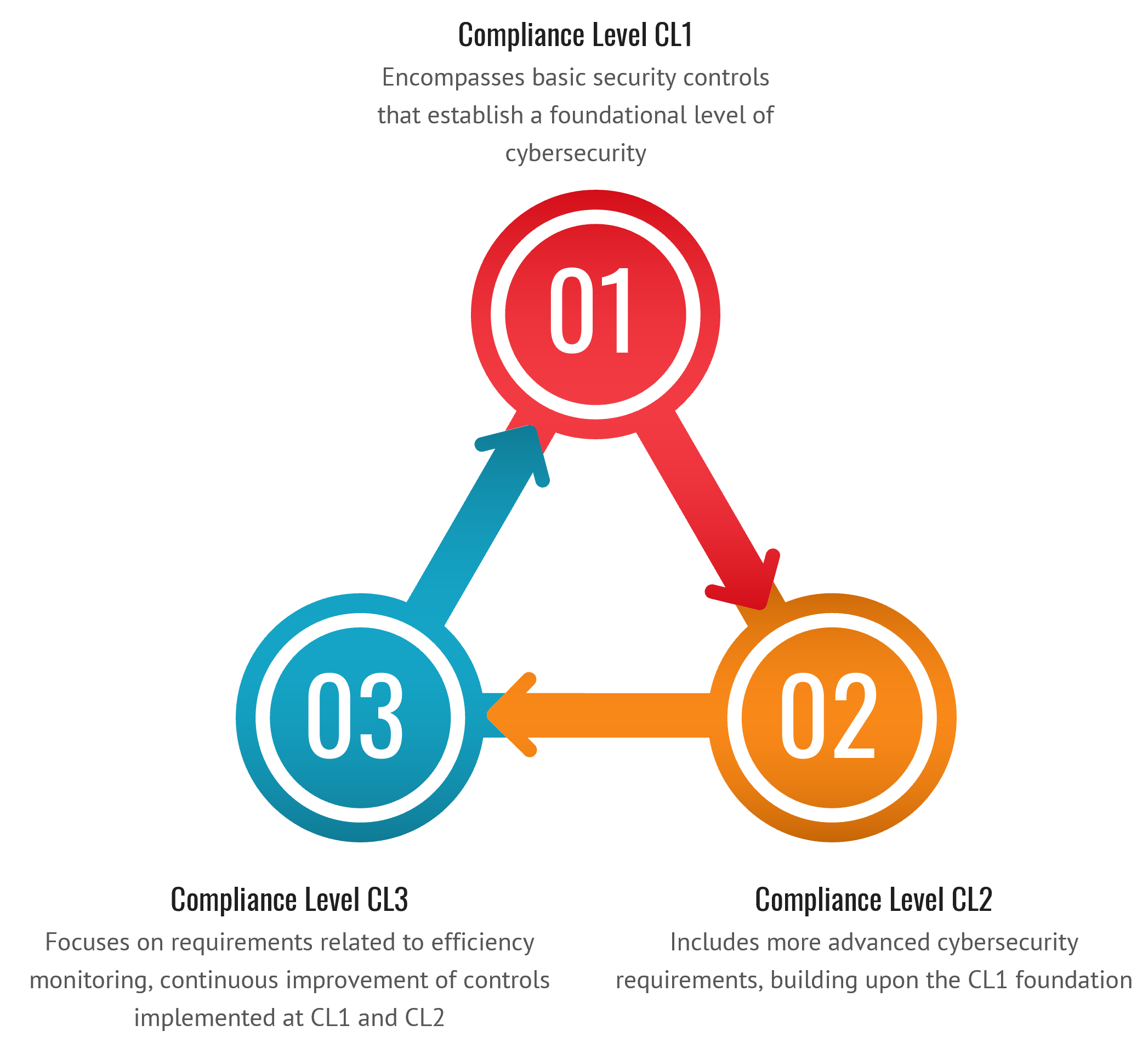
Compliance Levels (CL1, CL2, CL3)
CST CRF adopts a risk-based approach, structuring its requirements into three distinct compliance levels (CLs). This tiered system allows organizations to progressively enhance their cybersecurity capabilities:
-
Level 1: Includes the basic security controls.
-
Level 2: Includes advanced requirements.
-
Level 3: Includes requirements that are focusing on efficiency monitoring and contineous improvement to the controls on L1 & L2.
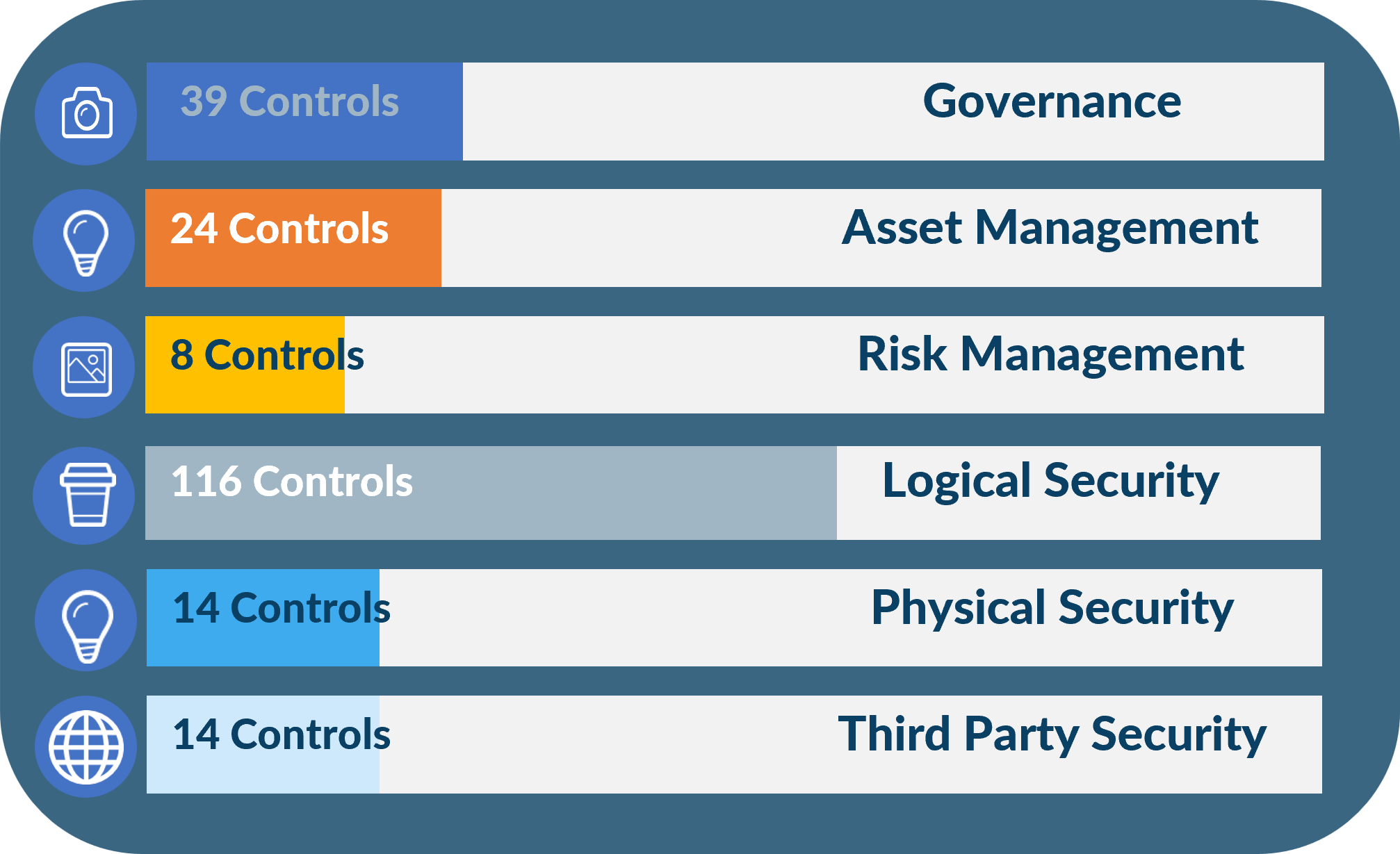
Key Control Domains
The CRF outlines an extensive array of control domains and sub-domains, ensuring a thorough approach to cybersecurity. CRF has six main domains and 215 controls.
The detailed and granular nature of these control domains, particularly within areas like Logical Security, implies a significant need for deep technical cybersecurity expertise for both the implementation and auditing phases.
How Cyberatos Can Help You ?
Cyberatos® provides a focused suite of GRC services to guide ICT Service Providers through the complexities of the CST CRF and help them achieve and sustain compliance, including the following approaches.
Also, we provide Auditing Services for CST CRF Assurance:
>> CRF Pre-Audits/Self-Assessment Facilitation: Helping organizations prepare for official CST audits by conducting comprehensive mock audits or facilitating structured self-assessments leveraging aspects of the official CRF audit form.
>> Corrective Action Planning and Support: Following a pre-audit or self-assessment, Cyberatos® assists in developing robust and prioritized corrective action plans to address identified gaps.



