Gap Analysis & Risk Assessments
We provide comprehensive information security Gap Analysis & Risk Quantification and Remediation Services
Understanding and addressing vulnerabilities is crucial for organizations of all sizes to protect their data and reputation from evolving threats
Understanding Risk Assessment
A cybersecurity risk assessment involves identifying, analyzing, and evaluating potential cybersecurity threats and vulnerabilities that could affect an organization’s information systems, data, or operations.
-
The assessment helps organizations to identify potential security risks, determine the likelihood and impact of these risks, and prioritize the implementation of appropriate cybersecurity controls to mitigate them.
-
Risk assessments are commonly performed leveraging industry-recognized frameworks such as NIST 800-30.
-
Risk assessments are also often required to comply with regulatory requirements and certification frameworks.
Understanding Gap Analysis
A cybersecurity gap assessment evaluates an organization’s current cybersecurity capabilities and processes against industry standards and best practices to identify gaps in an organization’s defenses.
- The assessment is designed to identify areas where an organization’s cybersecurity capabilities and processes may fall short of established standards or industry peers, or where additional controls are needed to mitigate potential risks.
-
Gap assessments are commonly performed leveraging industry-recognized frameworks such as NIST CSF, ISO 27001, or in line with regulatory compliance requirements such as SAMA CSF, CBJ, CST CRF, etc.
- Gap assessments are often performed as an input in the development of an organization’s strategic cybersecurity roadmap and are also utilized to benchmark organizations against industry peers.
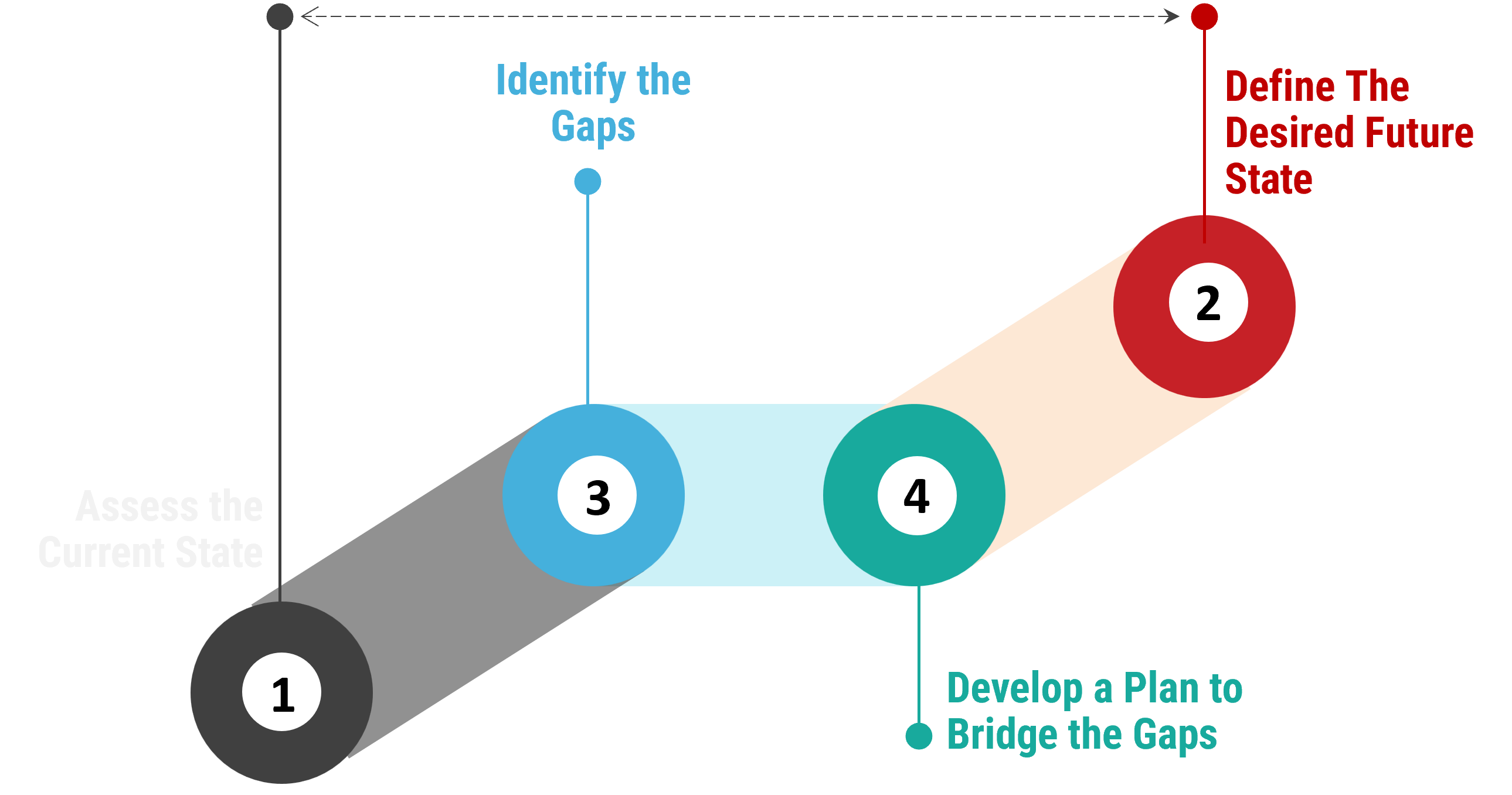
Cybersecurity Risk Assessments vs. Gap Assessments
Risk assessments and gap assessments should be viewed as complementary to one another:
- After completing a risk assessment, an organization may use the information gathered to prioritize which areas to focus on during a gap assessment.
- Alternatively, the outputs of a gap assessment may be utilized in a risk assessment to better understand an organization’s mitigating safeguards, thereby enabling the organization to better assess potential impacts and likelihoods of varying threat scenarios.
- Therefore, we recommend to conduct both risk assessments and gap assessments, often in parallel with one another, to obtain a holistic evaluation of the Organization's cybersecurity program.


















